Create security groups
Create security groups
In this step, we will proceed to create the security groups used for our instances. As you can see, these security groups will not need to open traditional ports to ssh like port 22 or remote desktop through port 3389.
Create security group for Linux instance located in public subnet
-
Go to VPC service management console
- Click Security Group.
- Click Create security group.
-
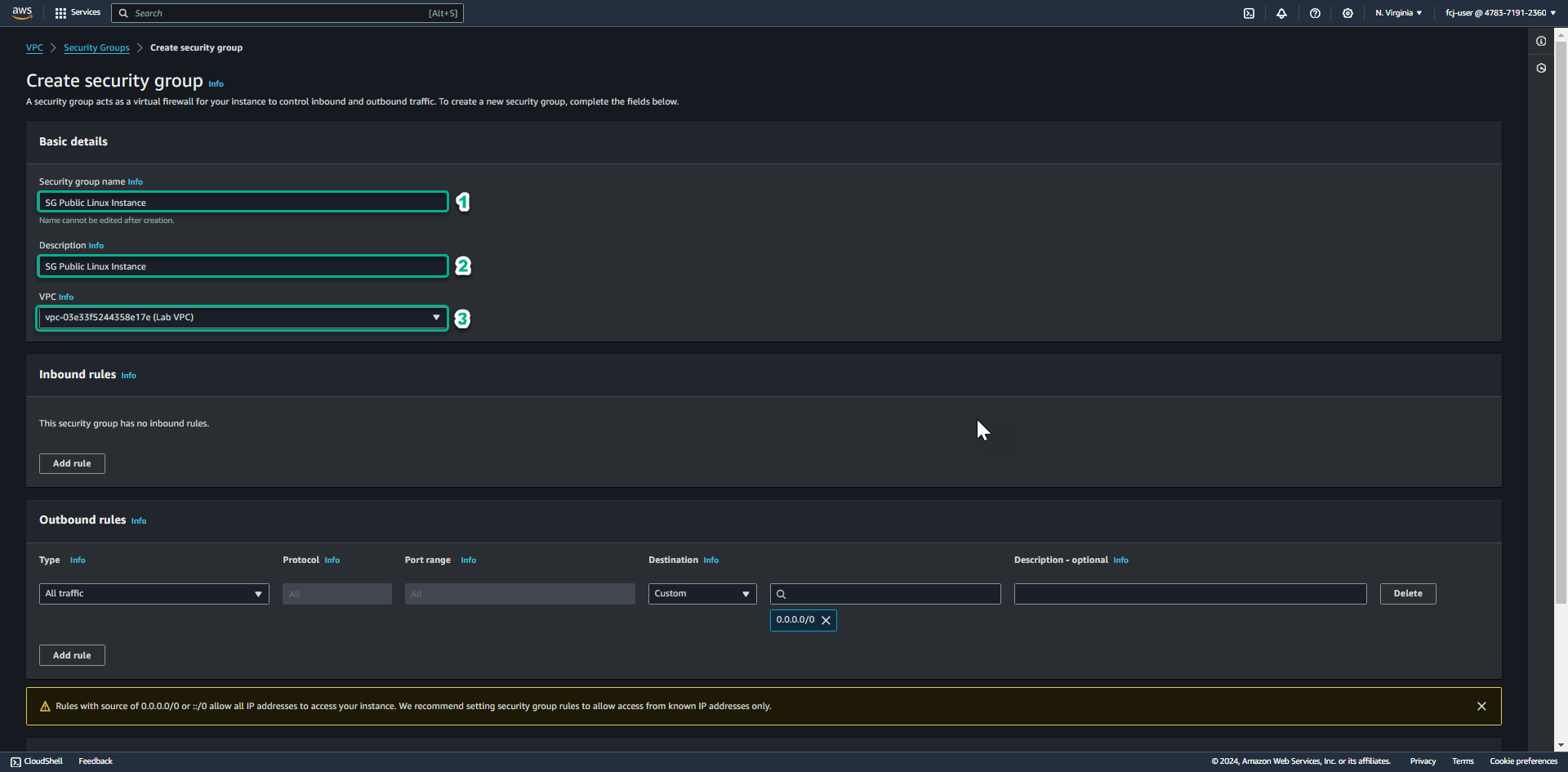
In the Security group name field, enter SG Public Linux Instance.
- In the Description section, enter SG Public Linux Instance.
- In the VPC section, click the X to reselect the Lab VPC you created for this lab.
-
Keep Outbound rule, drag the mouse to the bottom.
- Click Create security group.
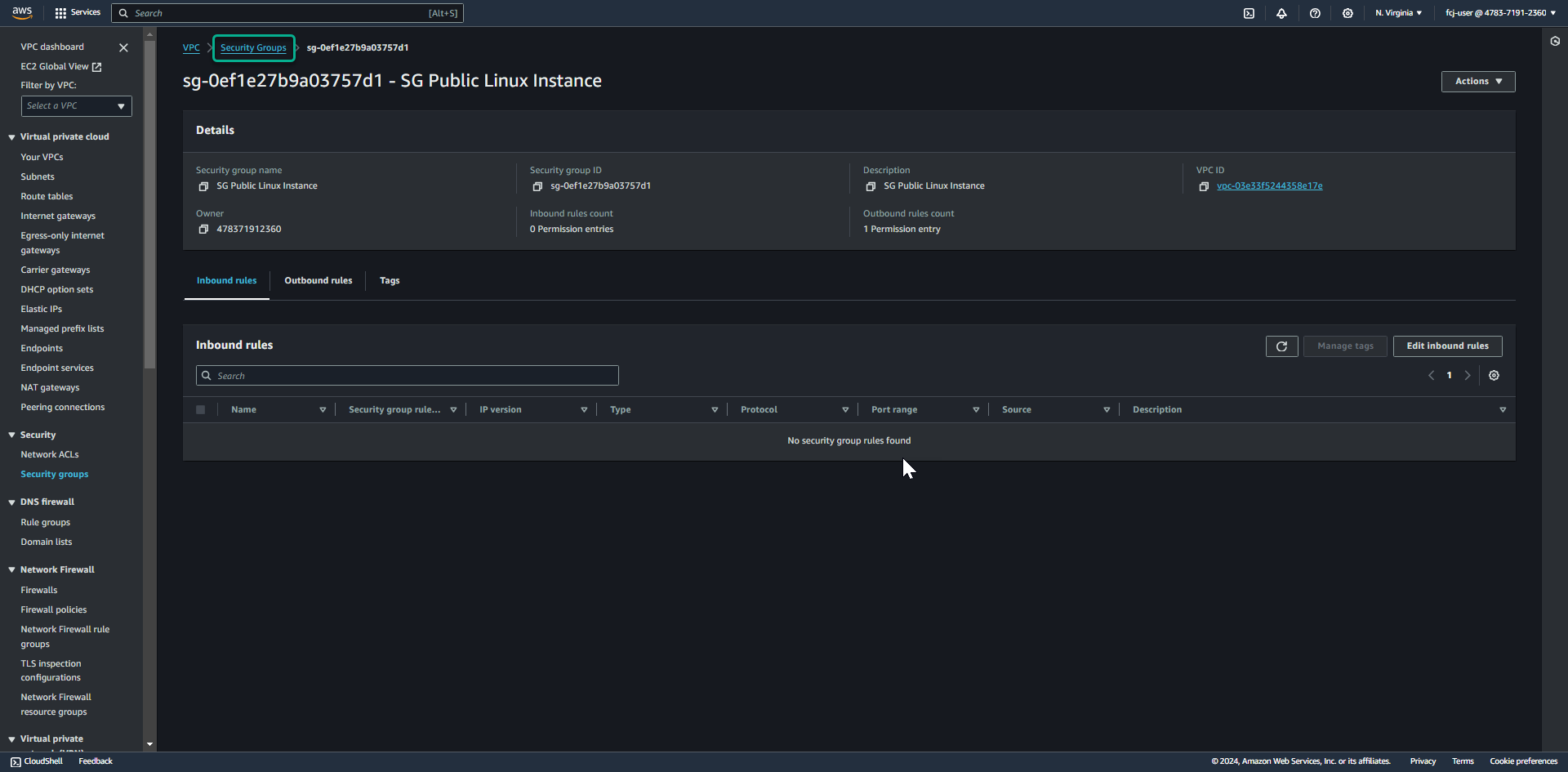
As you can see, the security group we created to use for Linux public instances will not need to open traditional ports to ssh like port 22.
Create a security group for a Windows instance located in a private subnet
-
After successfully creating a security group for the Linux instance located in the public subnet, click the Security Groups link to return to the Security groups list.
-
Click Create security group.
-
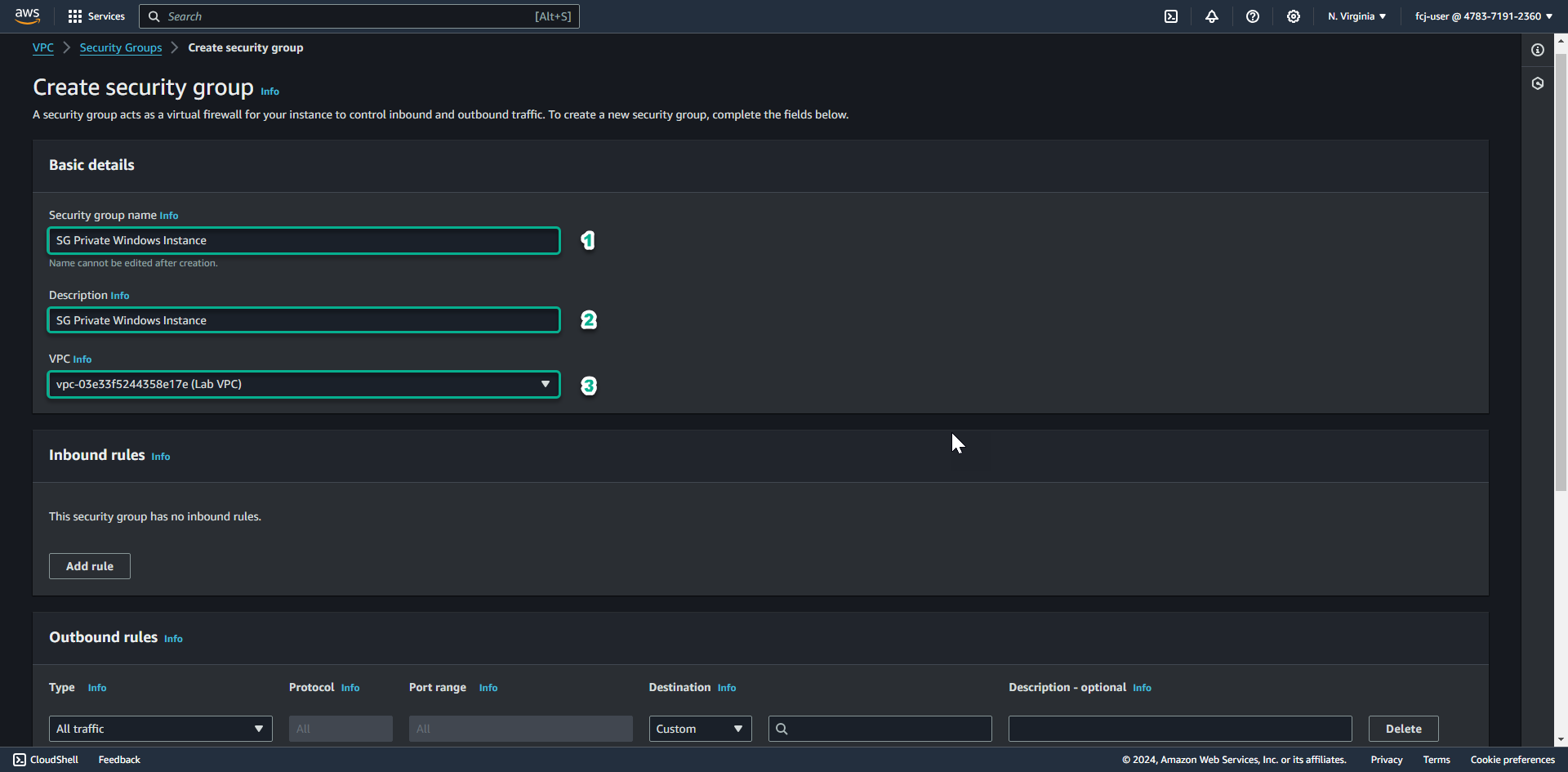
In the Security group name field, enter SG Private Windows Instance.
- In the Description section, enter SG Private Windows Instance.
- In the VPC section, click the X to reselect the Lab VPC you created for this lab.
-
Scroll down.
- Add Outbound rule to allow TCP 443 connection to 10.10.0.0/16 ( CIDR of Lab VPC we created)
- Click Create security group.
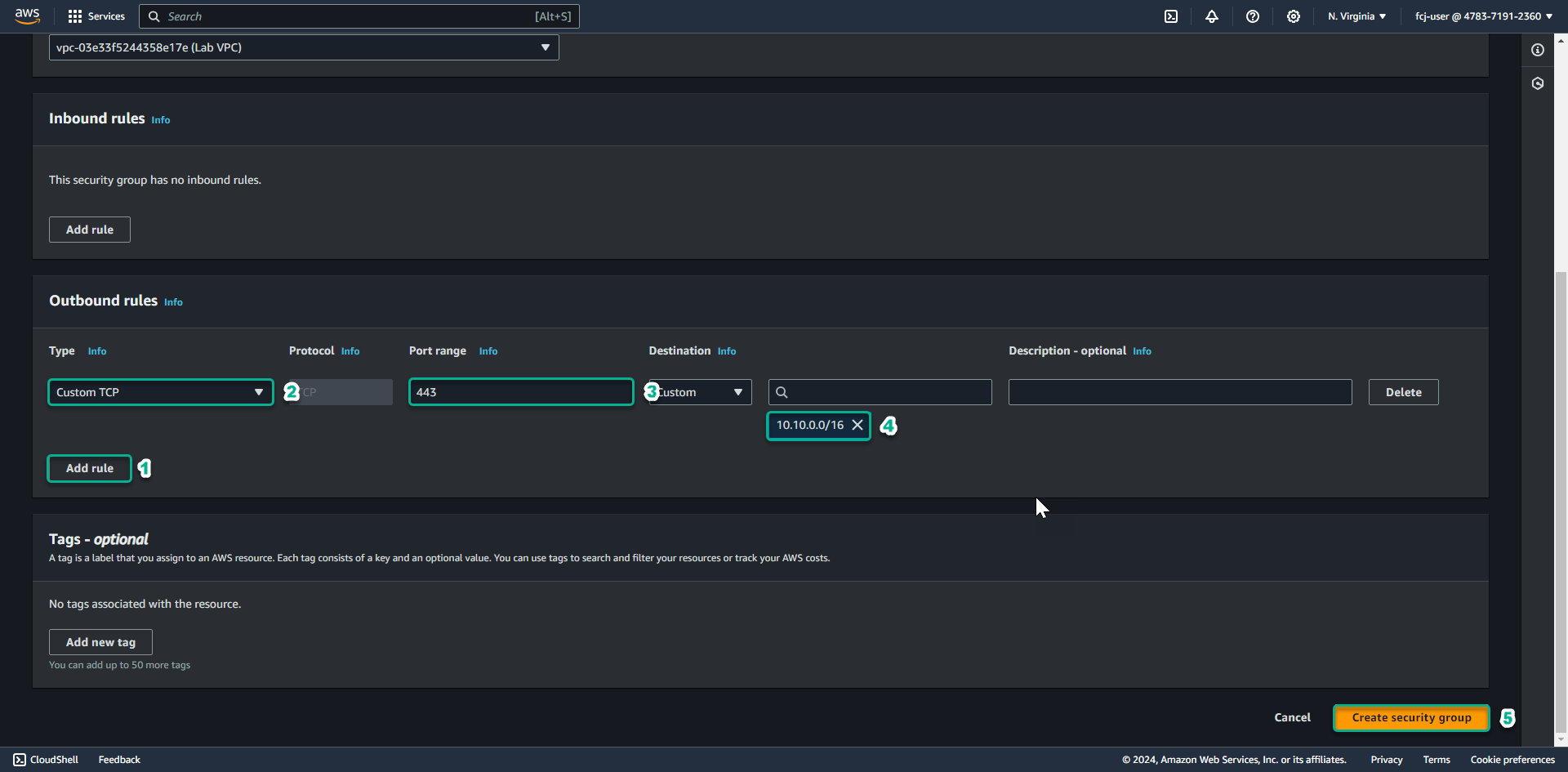
For the Instance in the private subnet, we will connect to the Session Manager endpoint over a TLS encrypted connection, so we need to allow outbound connection from our instance to VPC CIDR through port 443.
Create security group for VPC Endpoint
-
In this step, we will create security group for VPC Endpoint of Session Manager.
-
After successfully creating the security group for the Windows instance in the private subnet, click the Security Groups link to return to the Security groups list.
-
Click Create security group.
-
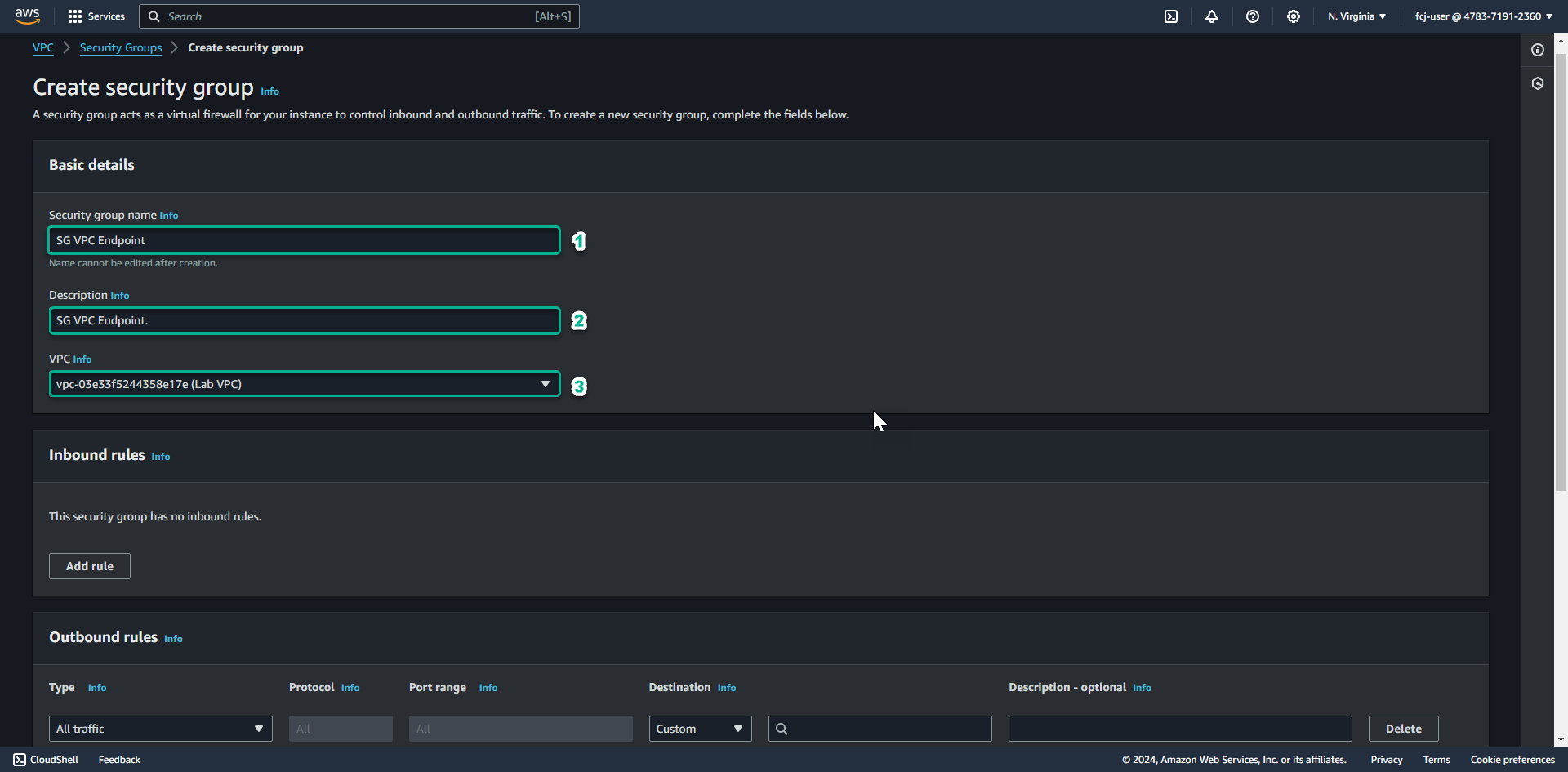
In the Security group name field, enter SG VPC Endpoint.
- In the Description section, enter SG VPC Endpoint.
- In the VPC section, click the X to reselect the Lab VPC you created for this lab.
-
Scroll down.
- Delete Outbound rule.
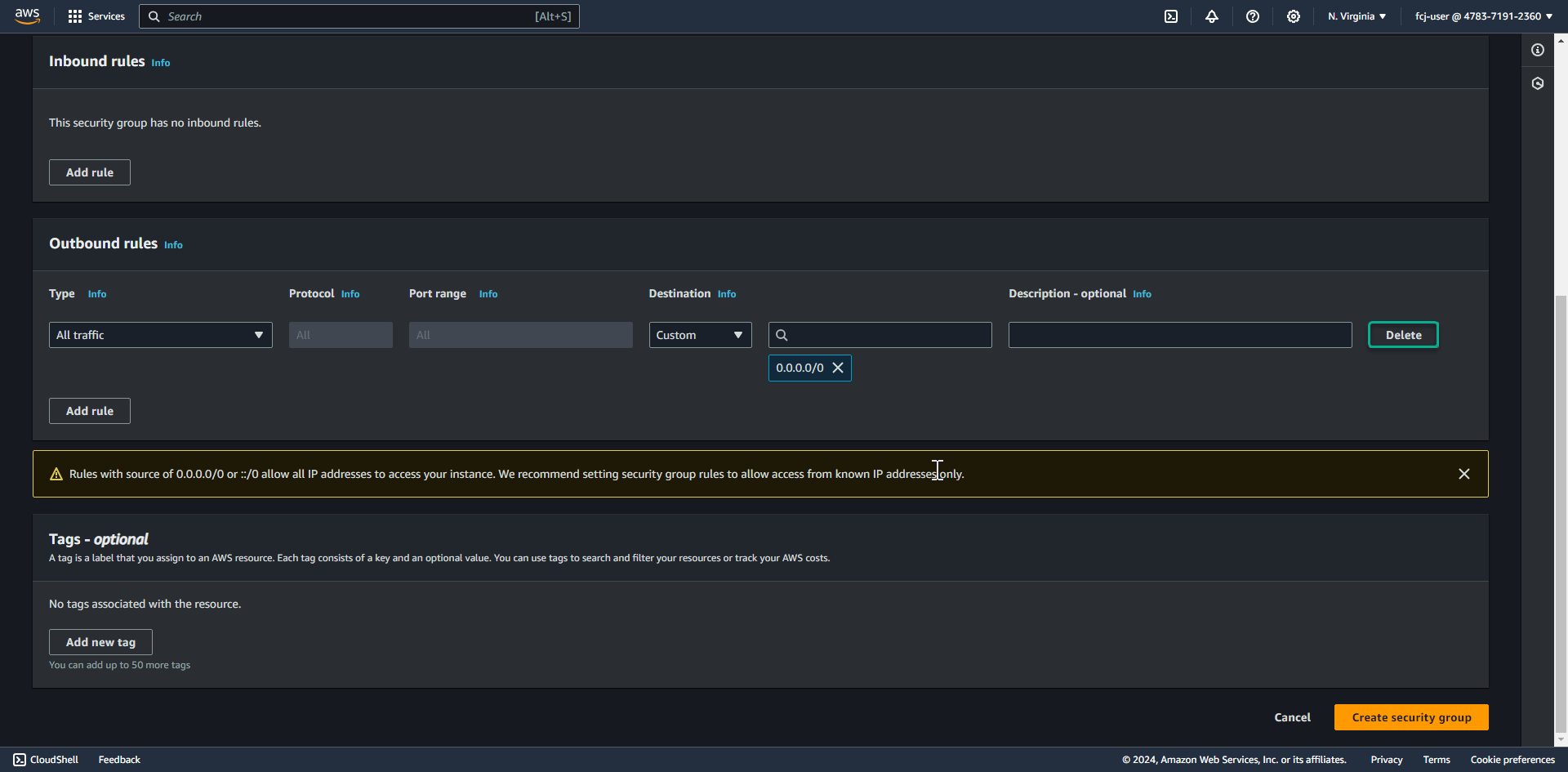
- Delete Outbound rule.
-
Add Inbound rule allowing TCP 443 to come from 10.10.0.0/16 ( CIDR of Lab VPC we created ).
- Click Create security group.
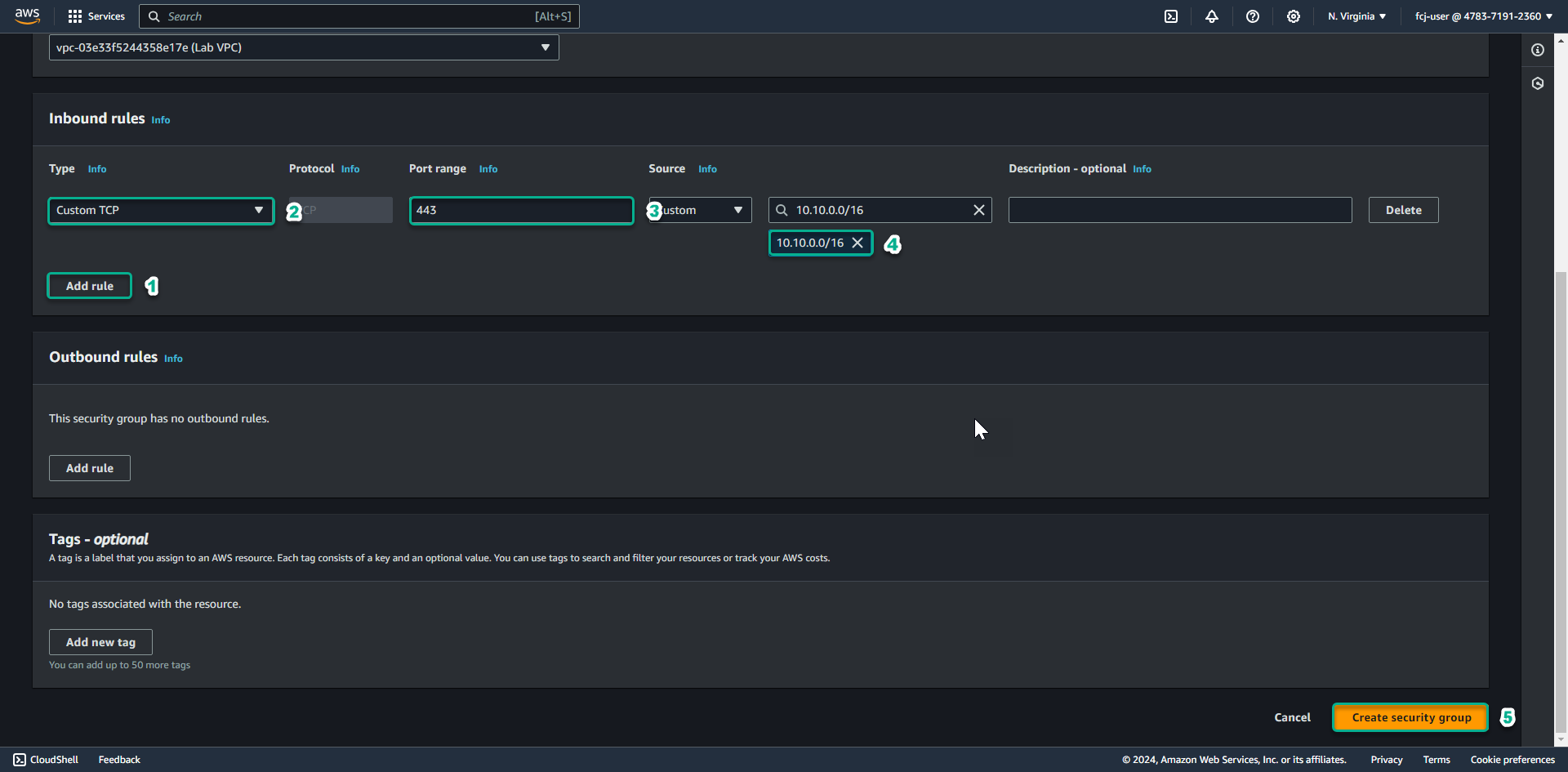
- Click Create security group.
So we are done creating the necessary security groups for EC2 instances and VPC Endpoints.