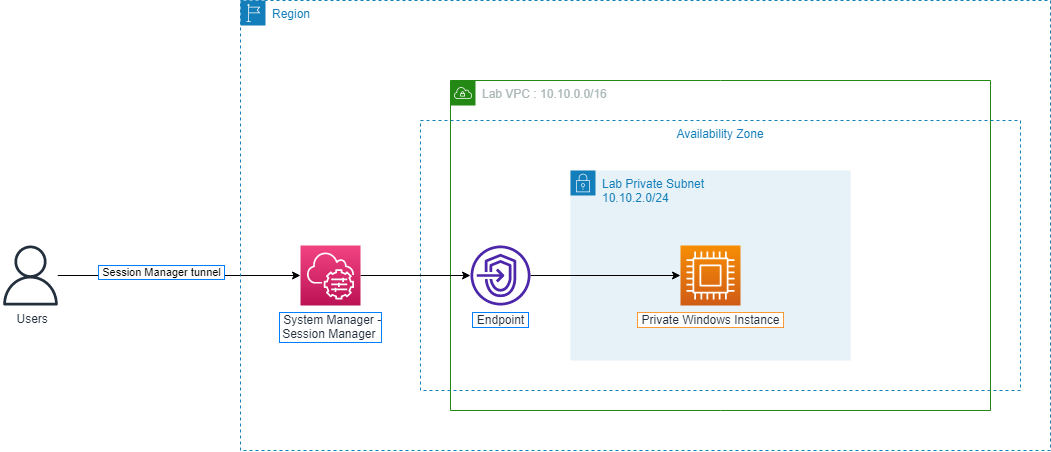
Port Forwarding
Port Forwarding is a useful way to redirect network traffic from one IP address - Port to another IP address - Port. With Port Forwarding we can access an EC2 instance located in the private subnet from our workstation.
We will configure Port Forwarding for the RDP connection between our machine and Private Windows Instance located in the private subnet we created for this exercise.
Create IAM user with permission to connect SSM
-
Go to IAM service management console
- Click Users , then click Create users.
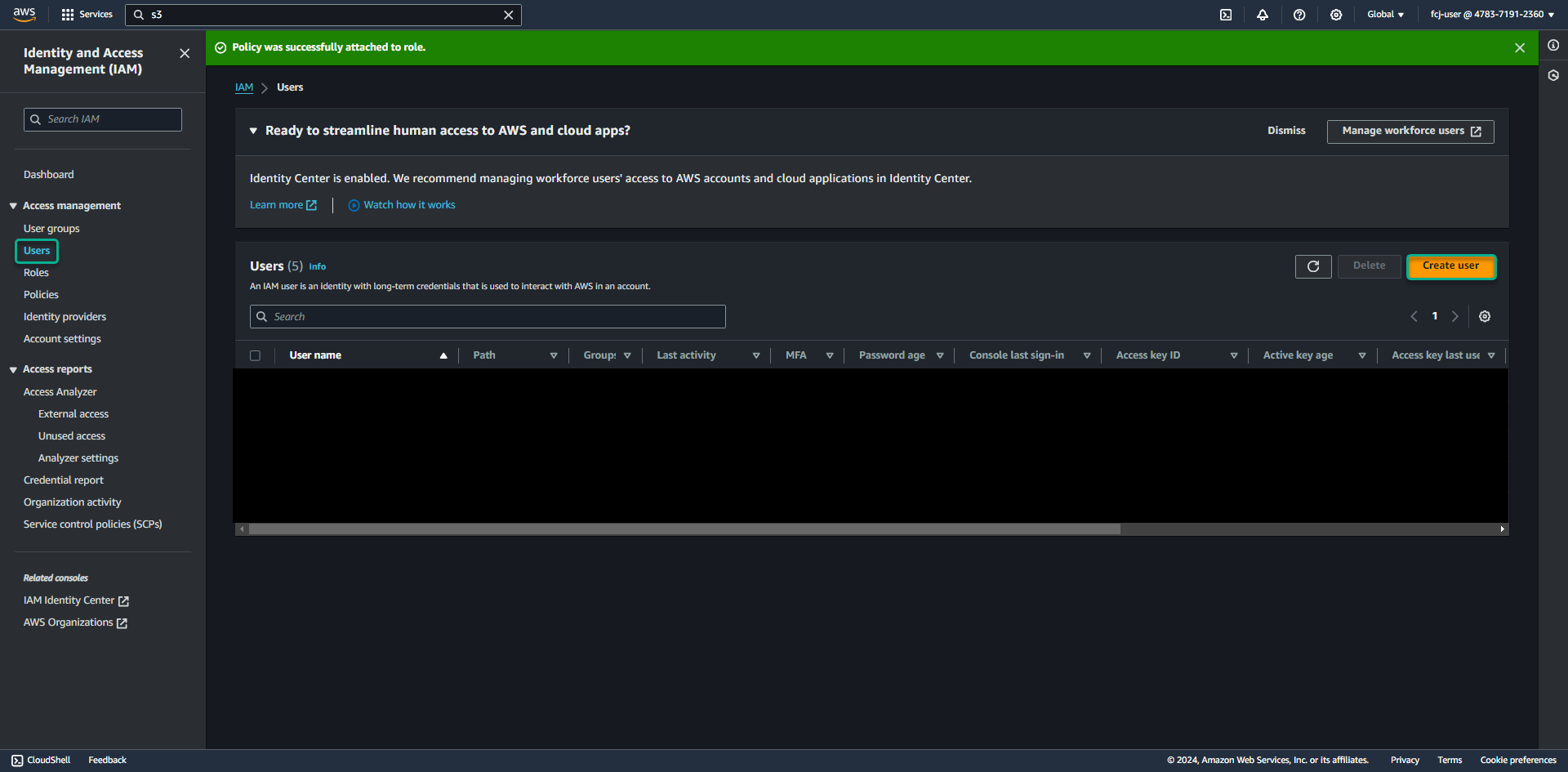
- Click Users , then click Create users.
-
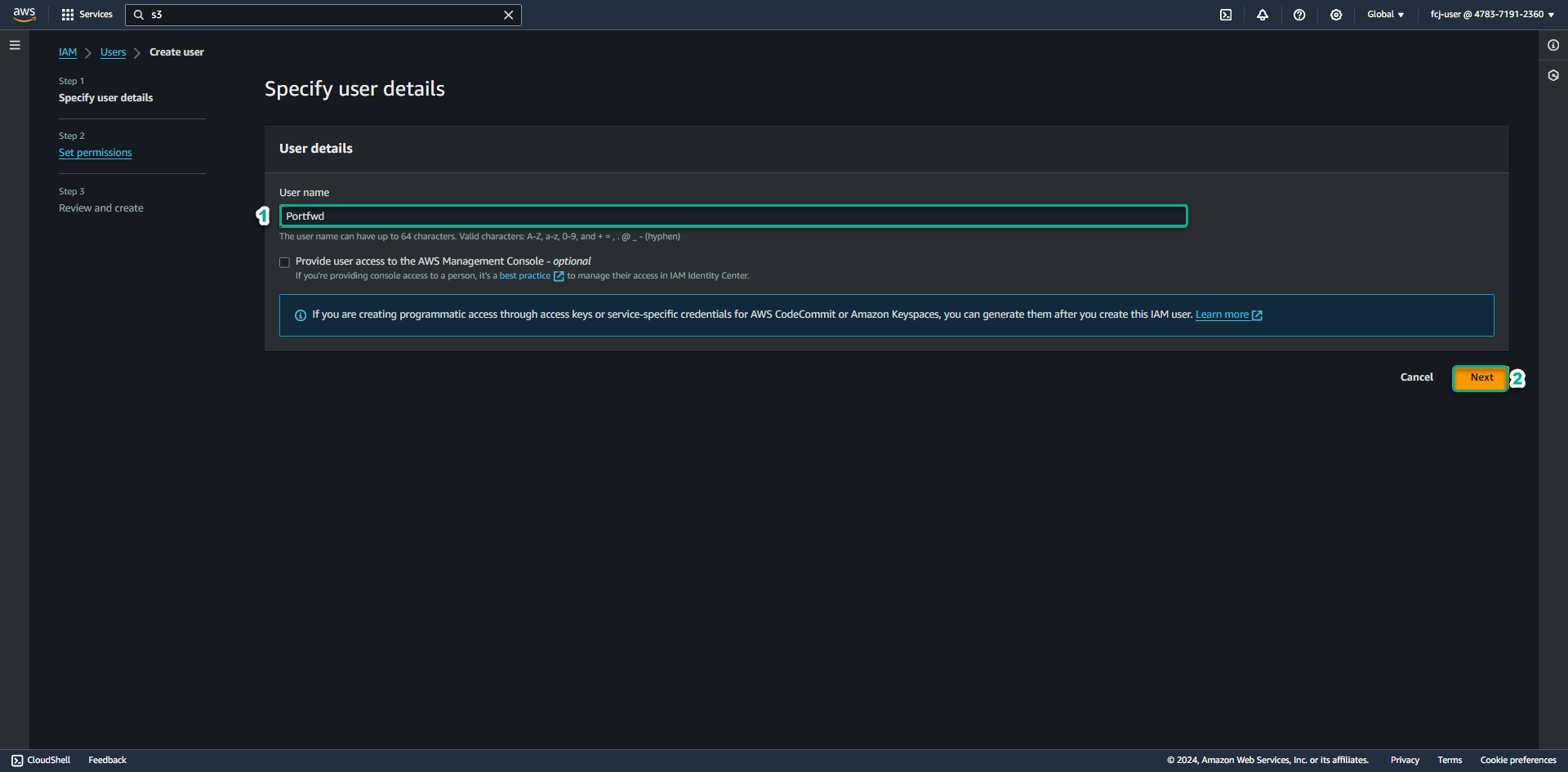
At the Create user page.
- In the User name field, enter Portfwd.
- Click Next.
-
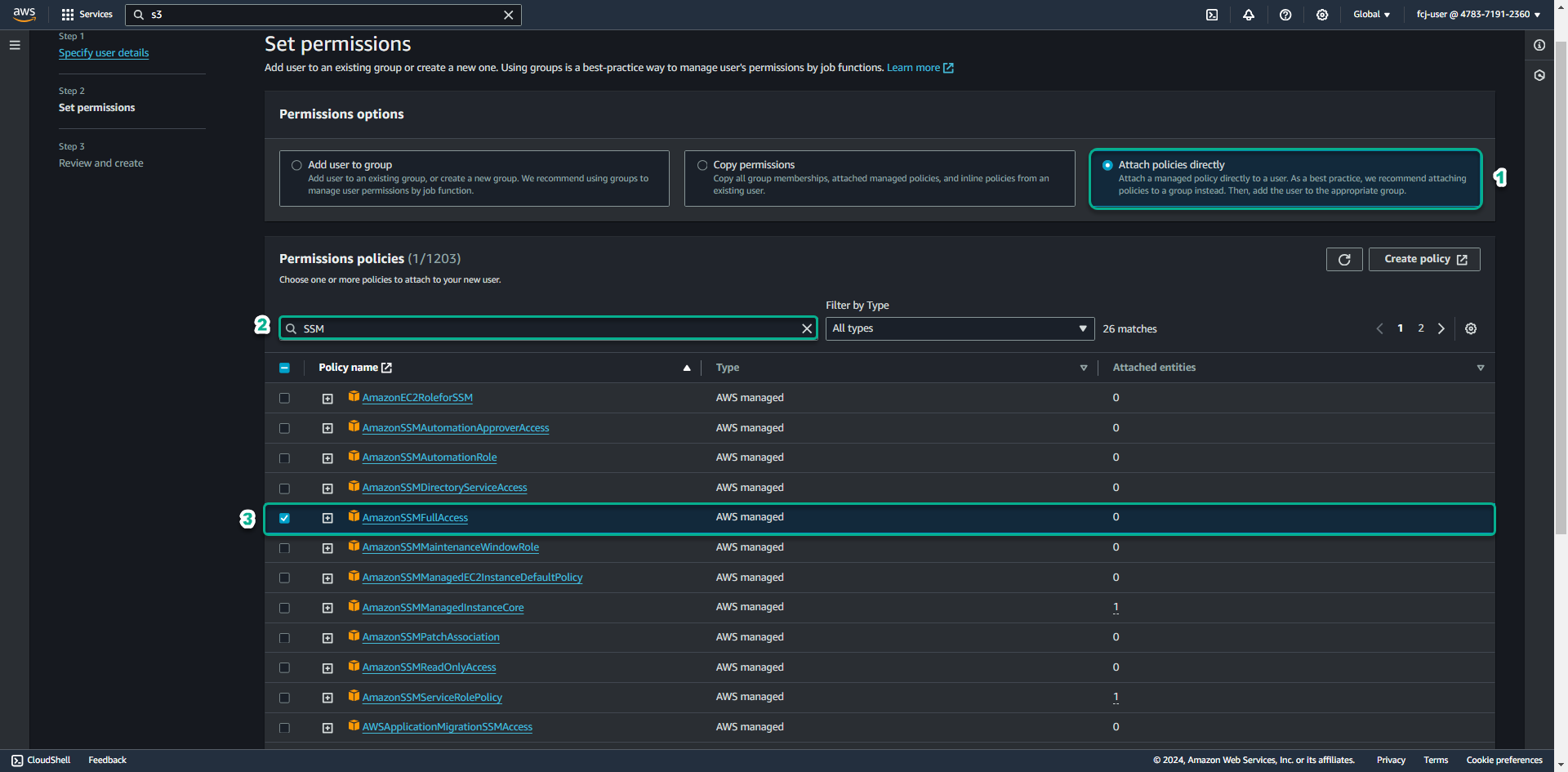
At the Set permission page
- Select Attach policies directly
- In the search box, enter ssm.
- Click on AmazonSSMFullAccess.
- Click Next, click Next: Reviews.
- Click Create user.
-
Create access key for Portfwd user
- Click Create access key
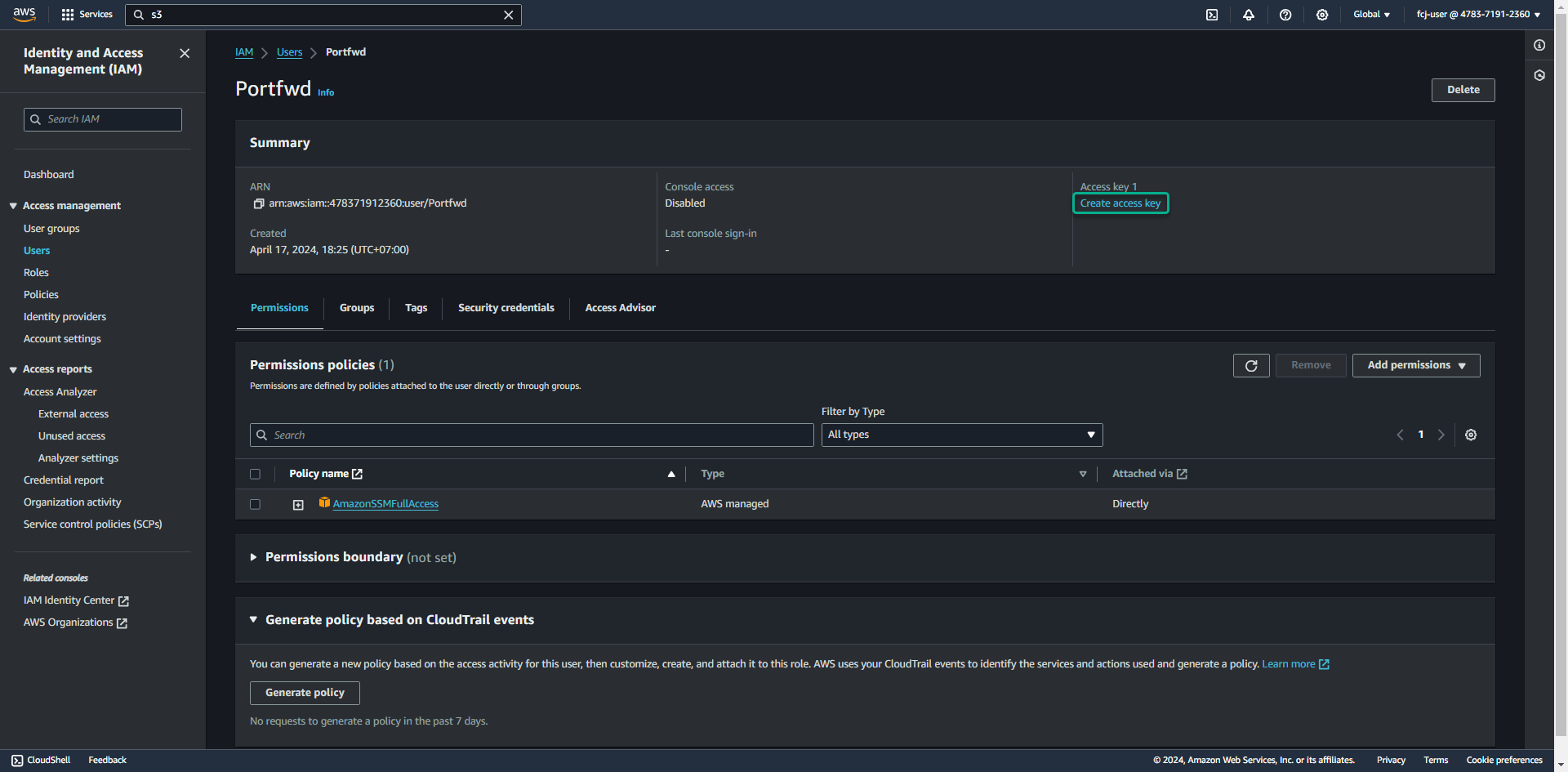
- Select Command Line Interface(CLI)
- Check box confirmation
- Click Next
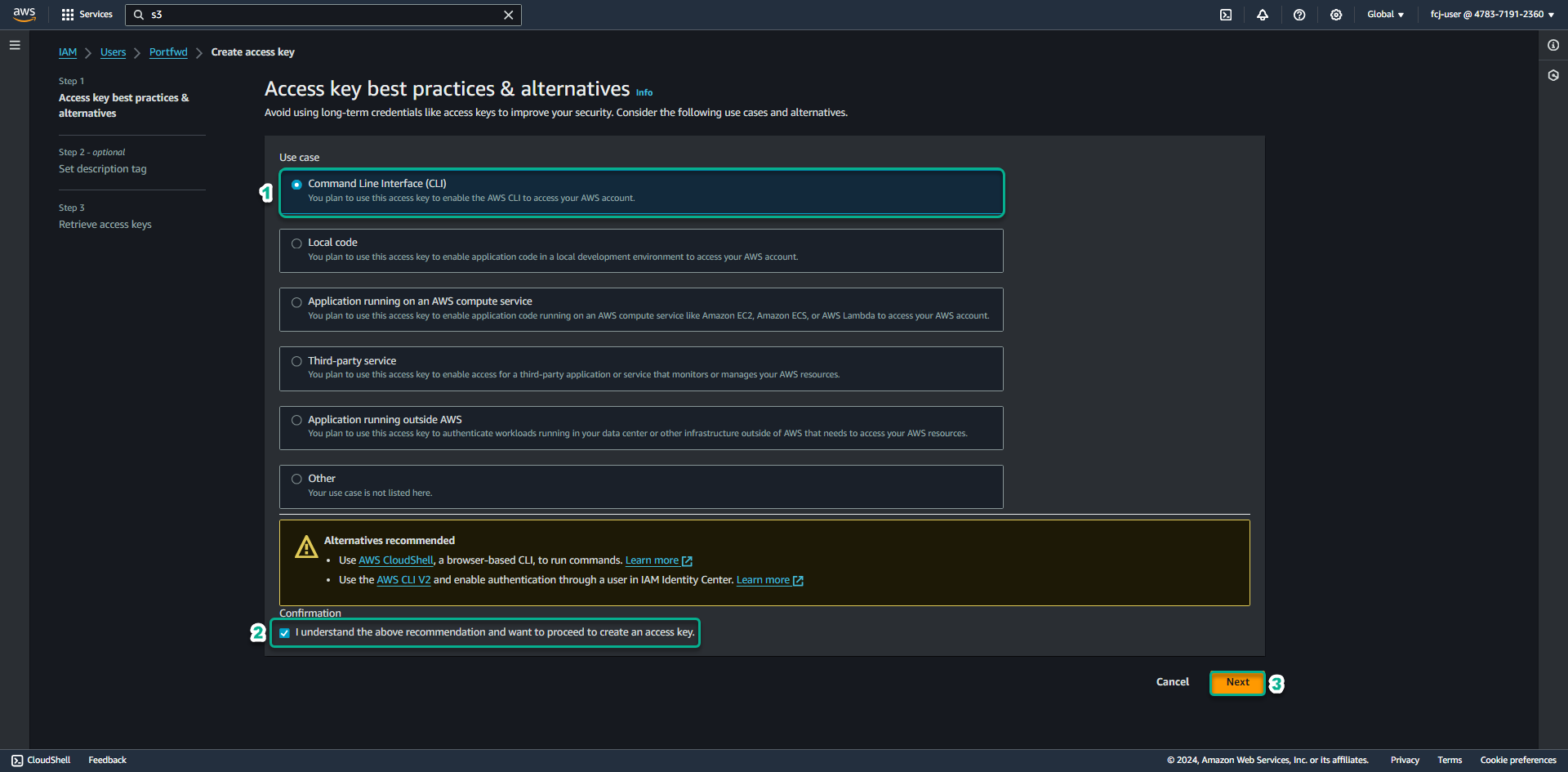
- Click Download.csv file
- Click Create access key
Save Access key ID and Secret access key information to perform AWS CLI configuration.
Install and Configure AWS CLI and Session Manager Plugin
To perform this hands-on, make sure your workstation has AWS CLI and Session Manager Plugin installed -manager-working-with-install-plugin.html)
More hands-on tutorials on installing and configuring the AWS CLI can be found here.
With Windows, when extracting the Session Manager Plugin installation folder, run the install.bat file with Administrator permission to perform the installation.
Implement Portforwarding
-
Run the command below in Command Prompt on your machine to configure Port Forwarding.
aws ssm start-session --target (your ID windows instance) --document-name AWS-StartPortForwardingSession --parameters portNumber="3389",localPortNumber="9999" --region (your region)Windows Private Instance Instance ID information can be found when you view the EC2 Windows Private Instance server details.
- Example command:
C:\Windows\system32>aws ssm start-session --target i-06343d7377486760c --document-name AWS-StartPortForwardingSession --parameters portNumber="3389",localPortNumber="9999" --region us-east-1If your command gives an error like below:
SessionManagerPlugin is not found. Please refer to SessionManager Documentation here: http://docs.aws.amazon.com/console/systems-manager/session-manager-plugin-not-found
Prove that you have not successfully installed the Session Manager Plugin. You may need to relaunch Command Prompt after installing Session Manager Plugin. -
Connect to the Private Windows Instance you created using the Remote Desktop tool on your workstation.
- In the Computer section: enter localhost:9999.
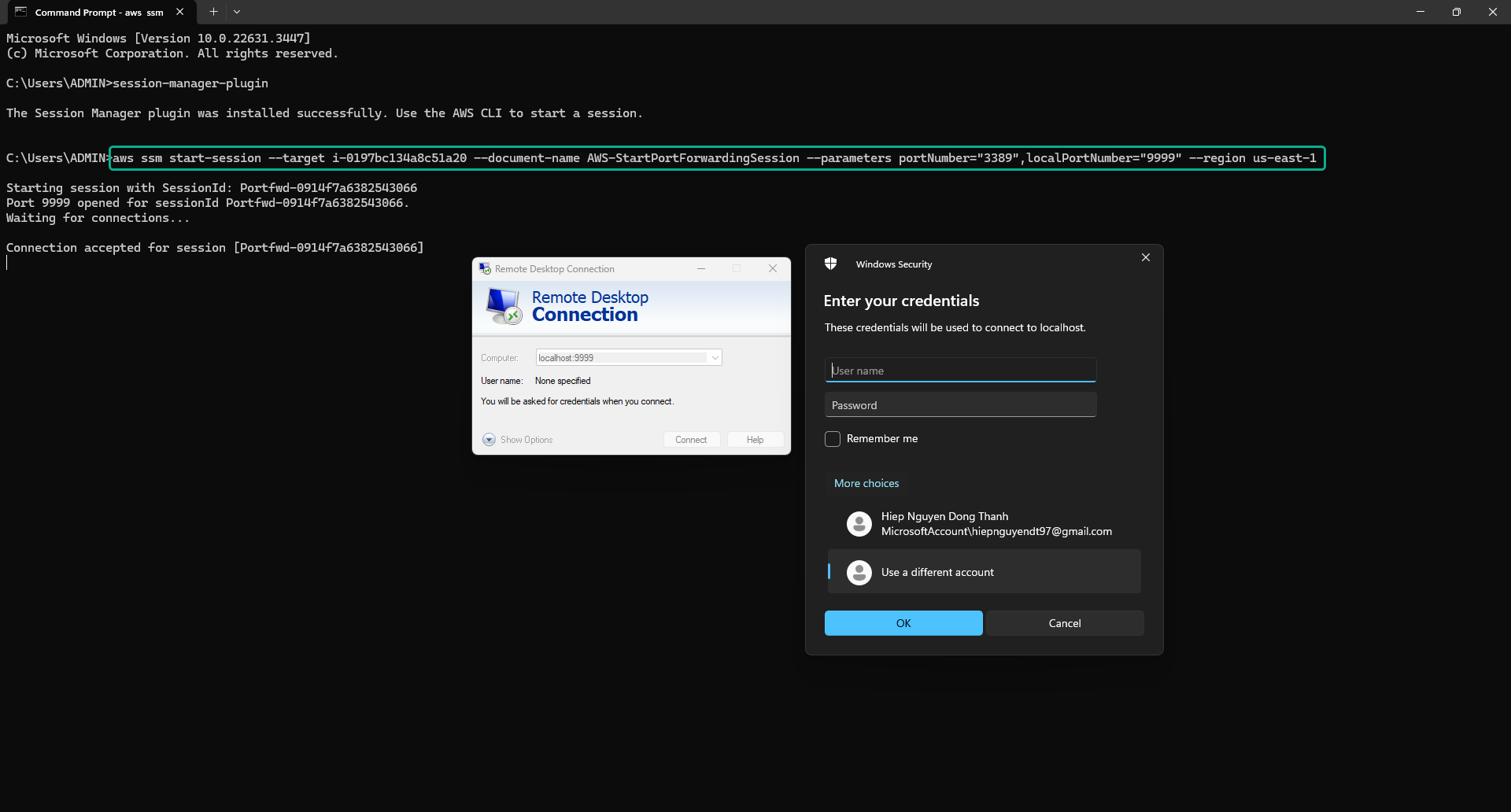
- In the Computer section: enter localhost:9999.
-
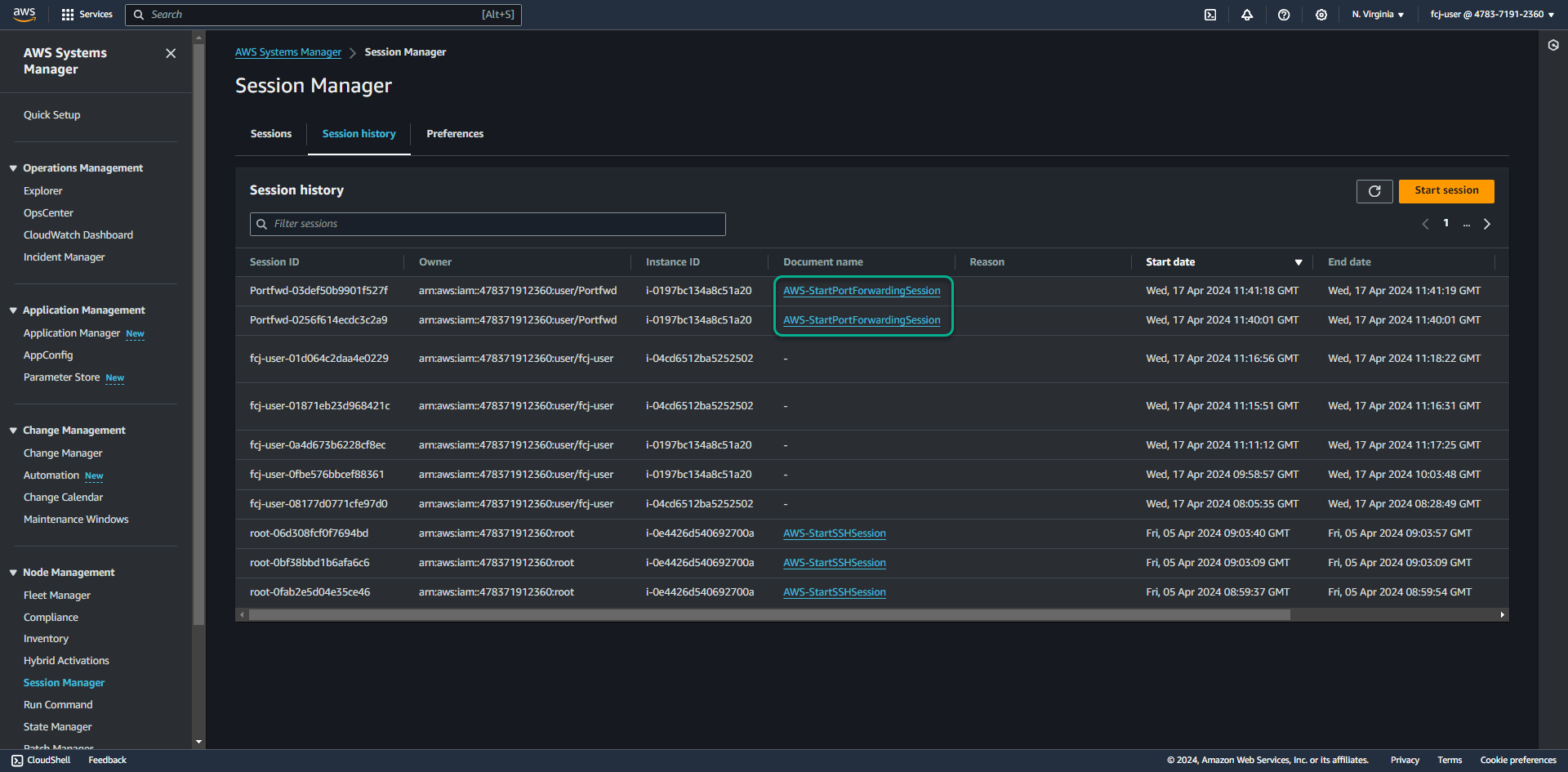
Return to the administration interface of the System Manager - Session Manager service.
- Click tab Session history.
- We will see session logs with Document name AWS-StartPortForwardingSession.
Congratulations on completing the lab on how to use Session Manager to connect and store session logs in S3 bucket. Remember to perform resource cleanup to avoid unintended costs.